With powerful hardware working together with an industry-leading camera system and intuitive AI experiences, everyday tasks have never been easier and faster
Processor exploits: what are affected companies saying?

The recent disclosure of exploits in several processors, chiefly Intel’s x86 chips, has resulted in a firestorm of controversy as companies scramble to fix the issue or deflect blame.
The exploits, discovered by Google researchers, involve the processor speculation feature in many chips, with Intel relying on this most aggressively. However, other companies are also affected by the news, so what are they saying?
Apple
The Cupertino company is also affected of course, using Intel chips in its Mac computers and the ARM instruction set in its iOS devices.
“All Mac systems and iOS devices are affected, but there are no known exploits impacting customers at this time,” read an excerpt from Apple’s website. It adds that it has already released updates against the first exploit for iOS 11.2, macOS 10.13.2, and tvOS 11.2, while it plans to release a Safari update to protect against the other exploits.
“We continue to develop and test further mitigations for these issues and will release them in upcoming updates of iOS, macOS, tvOS, and watchOS.”
ARM
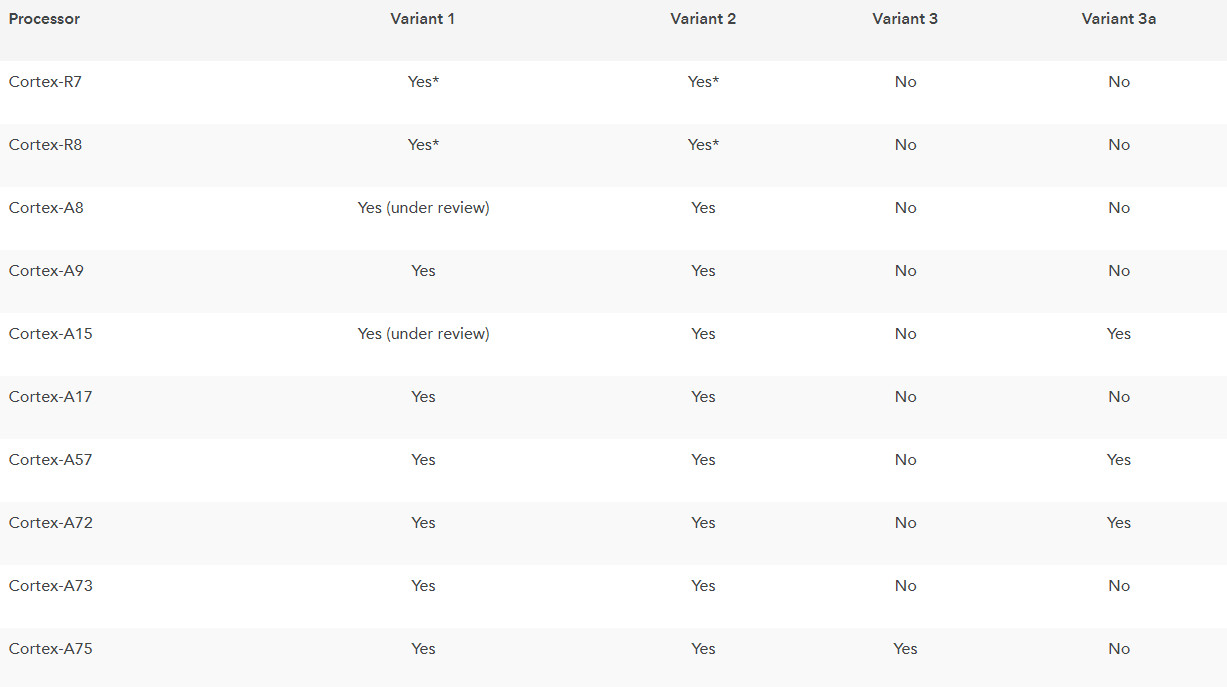
The company powering virtually all smartphones in some form has confirmed that its chips are also affected by the exploits, outlining the effects in a developer post.
ARM claims that the majority of ARM cores aren’t affected by the issue, with the A7, A53 and A55 cores notably absent from its table of affected hardware (see above).
AMD
The Intel rival has enjoyed a healthy 2017, but do these vulnerabilities put a damper on its 2018? Not quite, according to a post on the firm’s website.
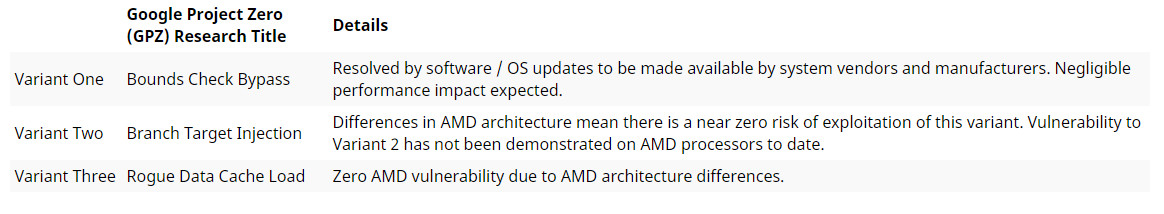
AMD claims that the first variant of the exploit will be resolved by software updates, while claiming that there is “near zero risk” of the second variant due to “differences” in AMD’s architecture. The chipmaker adds that its chips aren’t vulnerable to the third variant of the exploit. Check the above table for the rundown.
Google’s security researchers were behind the disclosure, so you’d expect the firm at large to be on top of things, right?
“In response to the vulnerabilities that were discovered we developed a novel mitigation called ‘Retpoline’ — a binary modification technique that protects against ‘branch target injection’ attacks. We shared Retpoline with our industry partners and have deployed it on Google’s systems, where we have observed negligible impact on performance,” read an excerpt of the firm’s post.
Google adds that it has also deployed a new technique, dubbed Kernel Page Table Isolation, to “the entire fleet of Google Linux production servers that support all of our products, including Search, Gmail, YouTube, and Google Cloud Platform”.
As for Android, Google claims that exploitation was “difficult and limited on the majority” of Android devices. Of course, mobile chip designer ARM has confirmed its vulnerability, but Google says the January 2018 security update is a first step.
“The Android 2018-01-05 Security Patch Level (SPL) includes mitigations reducing access to high precision timers that limit attacks on all known variants on ARM processors. These changes were released to Android partners in December 2017,” the firm explains, adding that future security updates would patch up the vulnerabilities as well.
“Users should accept the monthly updates for January 2018 on Nexus or their partner devices to receive these updates.”
Google Chrome users are also urged to enable the site isolation feature in their browser, but expect Chrome 64 (released on 23 January) to patch the security holes. Google says that future versions would include more “mitigations”.
Got a Chromebook? Then you should enable the site isolation feature too, while also ensuring that you’re running Chrome OS version 63 (which was pushed out on 15 December 2017).
Intel
The company already pushed out its side of the story earlier this week (as seen here), denying initial reports that only its chips were affected.
Of course, AMD and ARM have confirmed that their hardware is indeed affected, but not to the extent of Intel’s chips. The US chipmaker issued a follow-up statement on 4 January, clarifying the status of patches to fix the exploits.
“Intel has already issued updates for the majority of processor products introduced within the past five years. By the end of next week, Intel expects to have issued updates for more than 90 percent of processor products introduced within the past five years. In addition, many operating system vendors, public cloud service providers, device manufacturers and others have indicated that they have already updated their products and services,” read an update on the company website.
The chip colossus says it will continue to work on updates to mitigate the exploits.
Microsoft
According to The Register, Microsoft has issued an emergency update for Windows 10 users, but it’ll only install if your anti-virus program has been updated to support it.
“Due to an issue with some versions of anti-virus software, this fix is only being made applicable to the machines where the Anti virus ISV has updated the ALLOW REGKEY,” the firm noted on its website. Expect more Windows 10 updates to follow.