MTN South Africa has once again emerged as the country’s top-performing mobile network, securing the highest score in the Q2 2025 MyBroadband Network Quality…
Patch Tuesday April 2015: 4 critical updates, ‘Redirect to SMB’ unpatched
How time flies. It was just a year ago when Microsoft pushed its final updates to Windows XP, once its crowned jewel. This year though, and this month’s Patch Tuesday, saw a host of updates for its newer operating systems, Windows 7 and Windows 8, and a few for Microsoft Office as well.
This doesn’t quite tell the entire story though.
Prior to Patch Tuesday (this month falling on 14 April), a near-twenty-year-old vulnerability was found to be lurking in practically all of Microsoft’s OSes, and a number of software packages from various other vendors. But first, let’s talk about what Microsoft did address this past week.
Read more: Patch Tuesday March 2015: Stuxnet and FREAK patched, two updates causing issues
Bulletins totaled 11, with 26 vulnerabilities addressed across Microsoft’s software and OS expanse. Four were marked as critical, covering the likes of Internet Explorer, Microsoft Office, Internet Information Server and the company’s older OSes, from Windows 7 to Server 2003.
At the time of writing, no updates are reported to be causing issues on users’ machines.
Internet Explorer
With Project Spartan coming soon, we could expect patches for both of Microsoft’s browsers, but for now, the company addressed vulnerability that “could allow remote code execution if a user views a specially crafted webpage using Internet Explorer,” explains the bulletin.
“An attacker who successfully exploited these vulnerabilities could gain the same user rights as the current user.”
As it is rated Critical, it is suggested that this fix is installed as soon as possible.
“The security update addresses the vulnerabilities by modifying the way that Internet Explorer handles objects in memory and by helping to ensure that affected versions of Internet Explorer properly implement the ASLR security feature,” concludes the bulletin.
Microsoft Office
While IE wasn’t the only piece of software to receive a patch, Microsoft Word received a smaller but no less significant update, addressing a memory corruption flaw. Essentially, remote attackers could exploit said flaw by using corrupt DOCX document to access the user’s machine.
It seems that this vulnerability spans across Microsoft Word 2007 to 2013, and all the way down to Office for Mac, according to Symantec.
Windows’ EMF issue and Server vulnerability
Windows 7, Windows Vista, Windows Server 2003 and Windows Server 2008 received an important patch that addresses an issue with the EMF image format. Once again, the issue could allow a remote attacker to access the machine, by using a bogus EMF file.
Finally, largely affecting versions of Windows Server, the company addressed a vulnerability in the OS’s handling of particular HTTP requests.
“A remote code execution vulnerability exists in the HTTP protocol stack (HTTP.sys) that is caused when HTTP.sys improperly parses specially crafted HTTP requests. An attacker who successfully exploited this vulnerability could execute arbitrary code in the context of the System account.
“To exploit this vulnerability, an attacker would have to send a specially crafted HTTP request to the affected system. The update addresses the vulnerability by modifying how the Windows HTTP stack handles requests,” notes Microsoft.
There are a few additional patches, addressing vulnerabilities in Windows Hyper-V, .NET Framework and SharePoint. A complete list is available here.
What about Adobe?
Well, the company also released an update to Adobe Flash, which addresses “at least 22 flaws, including one flaw that is being actively exploited,” notes security expert Brian Krebs.
The latest version of Flash (at the time of writing) should boast version number 17.0.0.169. Nevertheless, the update should be fairly easy to find on the official Flash site.
‘Redirect to SMB’ found, affecting multiple vendors’ software
Above and beyond Patch Tuesday, security firm Cylance discovered a bit of a nasty lurking in the SMB protocol — usually used by those accessing files from a server.
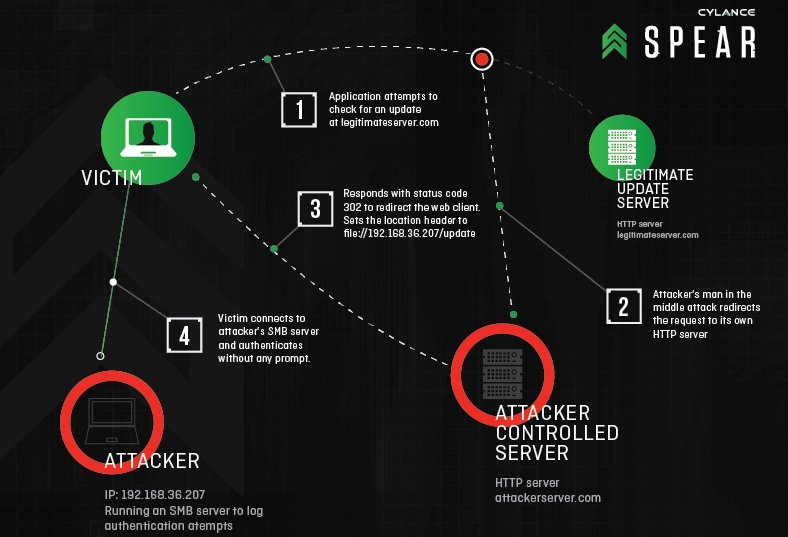
Redirect to SMB is a way for attackers to steal valuable user credentials by hijacking communications with legitimate web servers via man-in-the-middle attacks, then sending them to malicious SMB (server message block) servers that force them to spit out the victim’s username, domain and hashed password.
It sounds fairly scary, and it should be. The vulnerability has been alive and well for over 18 years. Perhaps the saving grace is that it’s not exactly easy to exploit.
Microsoft has yet to patch the vulnerability.
Updates to follow…
Feature image: Aaron Brady via Flickr

