South Africa’s retail forex industry is entering a decisive phase as regulation tightens and consolidation accelerates. What does it mean for brokers and traders?
Insane Android security flaw affects a potential 900-mil devices


Bluebox Labs, a “stealth startup” focused on mobile security, recently posted a fairly damning report that pokes holes in the integrity of almost every Android device ever. Team Bluebox say that any APK (Android Application Package File) can be injected with Trojan and snuck into the Google Play Store without the user even realizing it. In plain English, you could be downloading a Trojan virus from the Play Store without even realizing it.
Even worse, and according to Bluebox, this security flaw has been knocking around since Android 1.6 or “Donut”. This effectively places any Android device released over the last four years in danger. That’s well over 900-million devices, and the implications are quite frankly, horrendous to think about.
Trojan’s are a specific type of malware that give the hacker backdoor access to a device, once the Trojan has been installed. Other uses of a Trojan include: data theft, transferring funds once access to banking details have been established, drive formatting and more. In the right hands, your device becomes a puppet and the hackers are pulling the strings.
Outside of the possibility of Trojan-infected APK’s populating the app stores, Bluebox labs says that the risk is “compounded when applications are granted special elevated privileges within Android — specifically System UID access.” The system UID, or IMEI number is used by GSM networks to validate devices and if a hacker has access to this, they might as be the new owner of your phone. So that’s full access to the root Android systems and the network identifier itself, all from one infected APK file.
It’s all about the cryptographic signature, which Android uses to validate the legitimacy of APK’s. If the signature doesn’t match the one in the Android stores database, the app won’t install (unless you’ve ticked “install from unknown sources” on your android device). The security flaw, bug 8219321, goes around the cryptographic signature process and Android is tricked into installing a “clean” APK. Bluebox demonstrates the flaw with this screenshot indicating that the security team now has access to all device permissions.
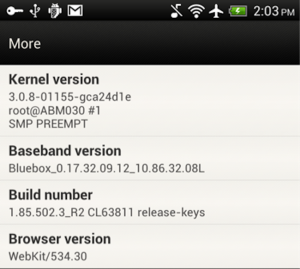
Now here’s what you can do to avoid being part of the 99%: check the publisher of each app (scroll to the bottom of the app info screen on the Play Store) and update your device to the latest version of Android. As Batman says, remain vigilant.


